
You can use the remote access account lockout feature to specify
how many times a remote access authentication has to fail against a
valid user account before the user is denied access. Use this tweak
to set the number of failed logins before the account is locked-out
and the time before the lockout is reset.
To do this, follow the next steps:
To change this, follow the next steps:
- Open the Registry Editor click on the Start button on
your taskbar, then click on Run and type "regedit"
and click on OK to start the regedit utility.
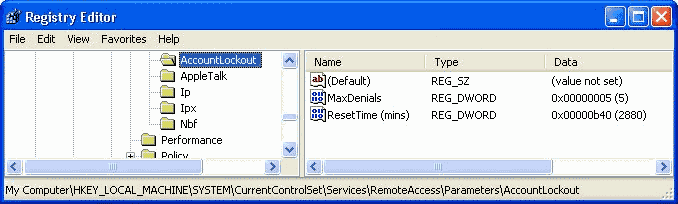
- Expand
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RemoteAccess\Parameters\AccountLockout
(see picture 1).
|
| Picture 1
|
- Create a new DWORD value or modify the existing value
called "MaxDenials" and set it to the number of failed
logins to lockout the account (or 0 to disable lockout).
- Create another DWORD value or modify the existing value
called "ResetTime (mins)" and set it to the time in minutes
that an account should remained locked-out. The default is 2,880
minutes (two days).
- The modifications you made will be in effect after you logout
or reboot your PC.
|


